Content
Check Your Ports – test udp port
Open Up Slot Examine Device:
A port is a number that represents an entry to a company that levels to the system.
In personal computer systems, an open port is actually a slot that presently uses (open) through a solution. An open port may be actually utilized to send or/and acquire records over the system.
- To scan individually, pick 'private', input a valid port number, and pick 'Check'.
- You can also make use of the Neighbor Map and Course Customer tools in ETS for a visible overview of how your network is transmitting.
- Discover product overviews, documents, training, onboarding info, and assistance posts.
- With the SNMP MIB browser, you can query SNMP-managed tools to see setups and various other MIB characteristics.
- Network ports are the communication endpoints for an equipment that is linked to the Internet.
- Ports differ in their procedures and the types of solutions they provide.
There are pair of recognized kinds of slots. TCP ports and UDP slots. Open port inspection device can examine the state of a TCP port. This may be done through sending a package utilizing the IPv4 (IP model 4) method.
An instance can easily be your web internet browser on the client-side as well as an internet hosting server as the remote hosting server.
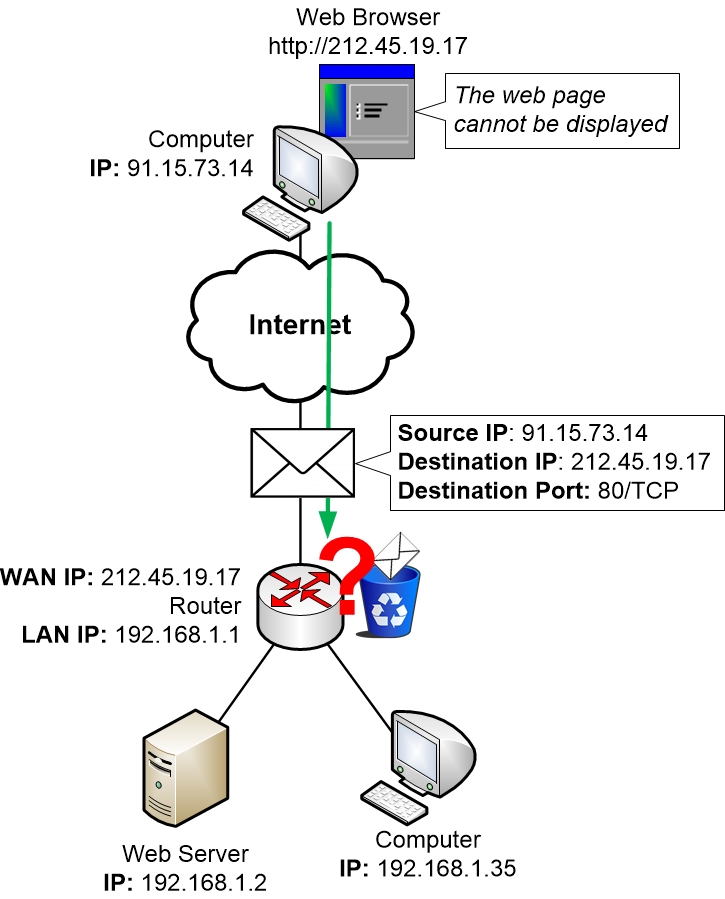
The web hosting server utilizes the default slot 80 for HTTP or slot 443 for HTTPS to stand by and listen closely for links. An available port inspection device may be made use of to inspect if the slot is presently open or even certainly not on an aim at machine.
It feels like a port test, using this resource you can easily additionally identify port sending status.
If your hosting server is being shut out through a firewall, you can easily additionally utilize an available port inspection tool to from another location check.
Port Scanning device: A port scanning device is a device that could be made use of to check a series of ports.
An additional sophisticated or even port checker can easily scan some deal with and even a full system hunting for slots that level. In computer system surveillance as well as hacking it is actually widely utilized to hunt for bothersome available ports that mean to be actually close or even monitor. An open slot is like an open door or even a window. Along with the correct understanding, it is actually possible to use this slot to enter right into the remote control computer.
Making use of and operating a frequent port check is actually a good technique to locate available ports as well as finalize them. , if an open slot is actually found it is additionally made use of to comprehend why as well as that open it.
.
What Is A Port Scanner? – port checker
There are some really valuable tools that can be actually made use of to scan the network deal with for available ports. Using such devices may even discover deal with inside the institution that needs to become taken out.
An instance of system ports scanner tool is Nmap. Advanced utilization of the resource can find what is actually the company (process) that open the operating and also the slot system backing this service.
On the internet slot scanning device:
The outdated craft of port scanning is still functioning. Also thou that today there is actually a more secure technique to shut as well as track slots and services in the workplace.
. A Breach diagnosis system (IDS) can be utilized to check the system.
Along with the evolved of new tools, an on the internet port scanning device device may be actually made use of as a source to scan a setting. Browsing coming from outside the institution.
An online port scanner is a port scanner like Article source any kind of various other slot scanning device. The only deferent is actually that it operates coming from outdoors your system. re: a website-- online.
It is a fantastic tool that could be utilized to examine if you possess needless available slots on your computer/device that needs to have to be actually finalized.
Solutions that count on the Internet (like web browsers, website page, and file transfer services) rely upon specific ports to transmit and receive information. Developers use file transfer protocols (FTPs) or SSH to run encrypted tunnels across computers to discuss relevant information in between bunches.
The moment a company is actually managing on a particular slot, you can not operate other solutions on it. Beginning Apache after you have actually currently started Nginx on port 80 will lead to a failed operation given that the slot is actually presently in make use of.

Open up ports end up being harmful when genuine services are actually capitalized on by means of protection weakness or malicious services are offered to a device by means of malware or social planning, cybercriminals can use these companies along with open ports to gain unwarranted accessibility to delicate information.
Closing unused ports reduces your surveillance threat through minimizing the amount of attack angles your association is actually subjected to.